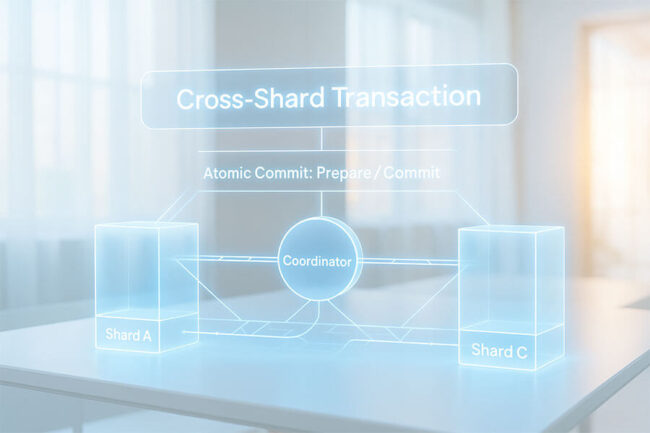
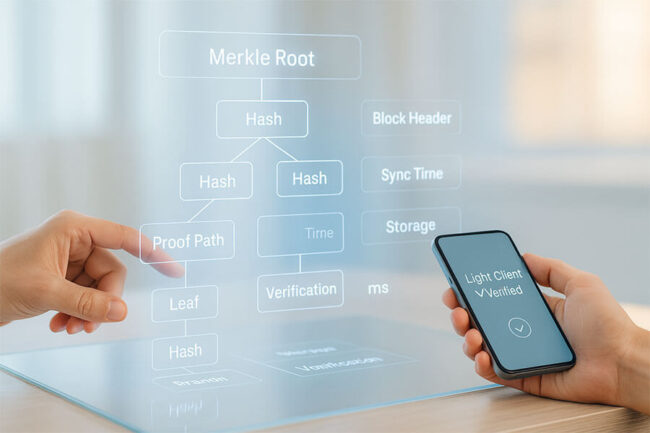
Decentralized Protocol Governance Evolution Patterns
The architecture of decision-making within blockchain protocols represents one of the most consequential developments in the evolution of digital infrastructure. As decentralized networks have grown from experimental projects into platforms managing billions of dollars in value, the mechanisms through which these systems evolve and adapt have become subjects of intense scrutiny and innovation. Governance in…
Read More